

CoffeeBean’s Identity and Access Platform consolidates multiple services for authentication including SSO, MFA, Adaptive Authentication, Social Login, etc. into a single and centralized solution for your apps and websites. The Access Management service brings security and good experience when users access your application.

CoffeeBean’s Identity and Access Platform consolidates multiple services for authentication including SSO, MFA, Adaptive Authentication, Social Login, etc into a single and centralized solution for your apps and websites.The Access Management service brings security and good experience when users access your application.


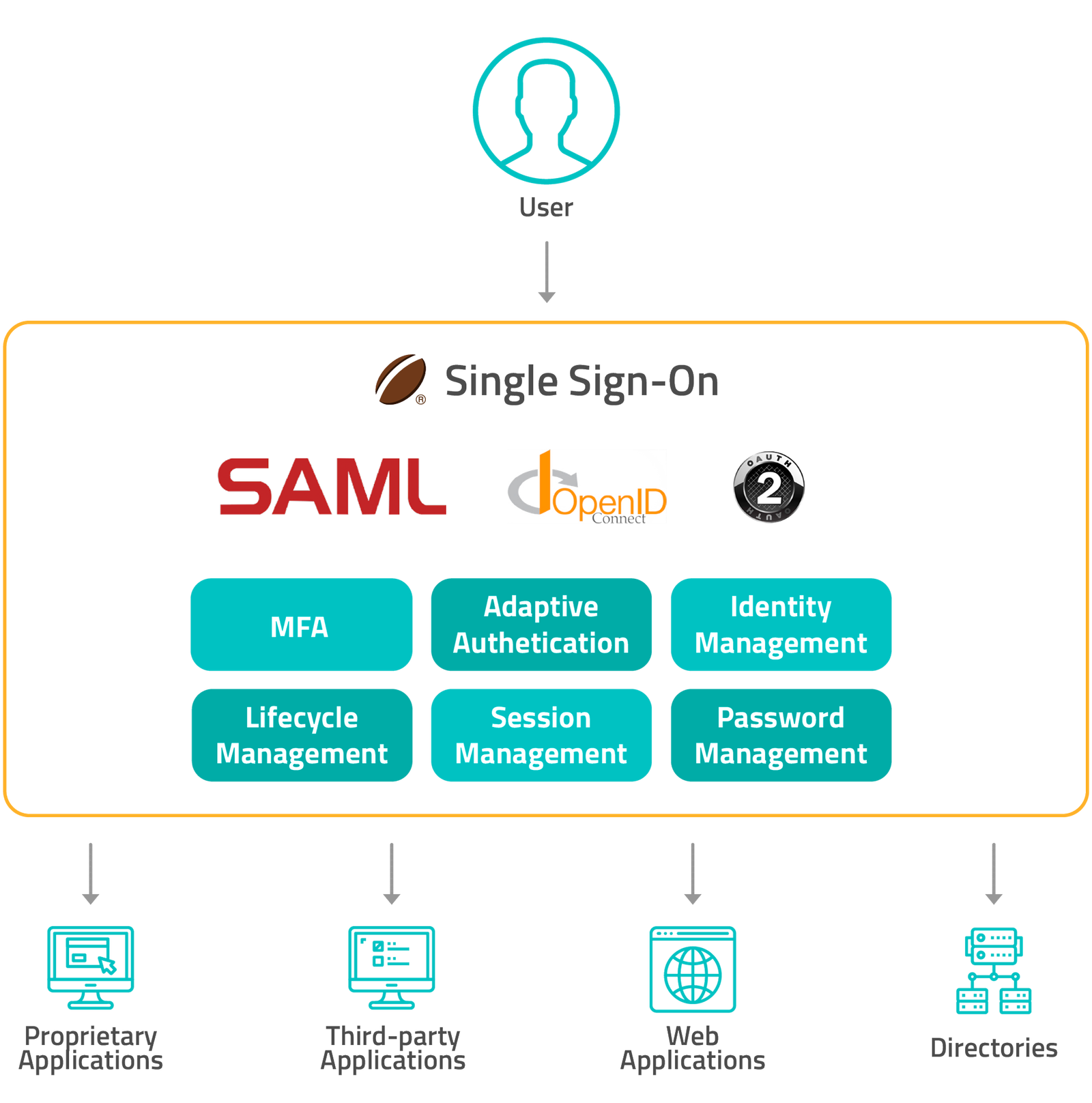
Single Sign-On
Single Sign-On (SSO) enables customers to login or register only once and gain access to all your websites or mobile apps without the need to login again. A single identity and authentication credentials are shared between all digital channels.

![]()
![]()
Experience
![]()
![]()
Federation
By using SSO you improve the user experience, since users don’t need to repeatedly log into your platforms. This feature also reduces support costs and site abandonment rates related to forgotten passwords.
Our SSO solution offers support for federation, acting as an Identity Provider (IdP) and enabling any type of user (customer, employee or partner) to access the resources they have permission to.


OpenID Connect and SAML
We offer a comprehensive support for SSO standards, such as SAML and OpenID Connect. This makes the process for identity federation and integration simpler.
![]()
![]()
Experience
By using SSO you improve the user experience, since users don’t need to repeatedly log into your platforms. This feature also reduces support costs and site abandonment rates related to forgotten passwords.
![]()
![]()
Federation
Our SSO solution offers support for federation, acting as an Identity Provider (IdP) and enabling any type of user (customer, employee or partner) to access the resources they have permission to.


OpenID Connect and SAML
We offer a comprehensive support for SSO standards, such as SAML and OpenID Connect. This makes the process for identity federation and integration simpler.

Multi-Factor Authentication (MFA)
Data breaches are making headlines weekly, concerning users and businesses. Multi-Factor Authentication (MFA) has become the standard to prevent unauthorized users from accessing solutions with passwords alone. CoffeeBean’s platform offers knowledge factors, possession factors and biometric factors to securely authenticate your users.
![]()
![]()
Biometrics and FIDO Standard
CoffeeBean is a member of the FIDO Alliance and follows FIDO protocols to offer biometrics (fingerprint, face recognition, iris recognition, etc.) as a single or second factor for authentication on mobile apps and websites. These protocols are also used for other types of factors such as PIN, hardware token, smart card, etc.
FIDO protocols guarantees a higher level of security since biometric data never leaves the device and the user is authenticated online using public key cryptography.
Some other benefits of using FIDO are:
- No secrets generated on the server side.
- No link-ability between services and accounts.
- FIDO Certification process provides interoperability between devices and servers.
- “Phishing”, “Man-In-The-Middle” and “Replay” attacks are avoided.
- Data breaches are self-contained and easily managed.

Quick and Easy to Install MFA Plugin
CoffeeBean introduces an easy to install MFA Plugin. It improves the security and reduces risk of data breaches by simply adding a second factor, which can be biometrics (FIDO protocol) or One Time Password (OTP).
- MFA plug-and-play solution
- Simple and easy to integrate with already existing systems
- Increase authentication security
- Biometrics using FIDO Protocol
- OTP based on Email, SMS, WhatsApp or third-party apps
![]()
![]()
One-Time Password
CoffeeBean offers OTP through different channels such as SMS, email, WhatsApp, push notifications and third-party apps (Google Authenticator, Duo, etc).
![]()
![]()
Passwordless
Biometrics, OTP and hardware tokens can be used to replace passwords, improving security and user experience.
![]()
![]()
Biometrics and FIDO Standard
CoffeeBean is a member of the FIDO Alliance and follows FIDO protocols to offer biometrics (fingerprint, face recognition, iris recognition, etc.) as a single or second factor for authentication on mobile apps and websites. These protocols are also used for other types of factors such as PIN, hardware token, smart card, etc.
FIDO protocols guarantees a higher level of security since biometric data never leaves the device and the user is authenticated online using public key cryptography.
Some other benefits of using FIDO are:
- No secrets generated on the server side.
- No link-ability between services and accounts.
- FIDO Certification process provides interoperability between devices and servers.
- “Phishing”, “Man-In-The-Middle” and “Replay” attacks are avoided.
- Data breaches are self-contained and easily managed.
![]()
![]()
Quick and Easy to Install MFA Plugin
CoffeeBean introduces an easy to install MFA Plugin. It improves the security and reduces risk of data breaches by simply adding a second factor, which can be biometrics (FIDO protocol) or One Time Password (OTP).
- MFA plug-and-play solution
- Simple and easy to integrate with already existing systems
- Increase authentication security
- Biometrics using FIDO Protocol
- OTP based on Email, SMS, WhatsApp or third-party apps
![]()
![]()
One-Time Password
CoffeeBean offers OTP through different channels such as SMS, email, WhatsApp, push notifications and third-party apps (Google Authenticator, Duo, etc).
![]()
![]()
Passwordless
Biometrics, OTP and hardware tokens can be used to replace passwords, improving security and user experience.
![]()
![]()
Single Integration Point for Social Networks
CoffeeBean simplifies the integration with social networks by providing a single API instead of having to integrate with each social networks’ APIs. Additionally, the platform keeps up to date with the latest API versions released by the social networks.
![]()
![]()
Social Networks Support
Today CoffeeBean offers social login using the main social networks (Facebook, Twitter, Google, LinkedIn, Instagram) and easily integrates with others through OAuth2/OAuth1 protocols.
![]()
![]()
Know Your Customer
By using social login you can capture permission-based identity data such as customer interests, activities and preferences. This information can then be used to provide more relevant content to your customers.
![]()
![]()
Social Networks Compliance
Social networks like Facebook enforce compliance rules through their terms of service, such as data deletion requests, deauthorization, data update, consent changes and webhooks. CoffeeBean automatically integrates with social networks to adhere to their privacy policies.
![]()
![]()
Single Integration Point for Social Networks
CoffeeBean simplifies the integration with social networks by providing a single API instead of having to integrate with each social networks’ APIs. Additionally, the platform keeps up to date with the latest API versions released by the social networks.

Social Networks Support
Today CoffeeBean offers social login using the main social networks (Facebook, Twitter, Google, LinkedIn, Instagram) and easily integrates with others through OAuth2/OAuth1 protocols.
![]()
![]()
Know Your Customer
By using social login you can capture permission-based identity data such as customer interests, activities and preferences. This information can then be used to provide more relevant content to your customers.


Social Networks Compliance
Social networks like Facebook enforce compliance rules through their terms of service, such as data deletion requests, deauthorization, data update, consent changes and webhooks. CoffeeBean automatically integrates with social networks to adhere to their privacy policies.


Authentication Intelligence
Capturing and storing information regarding users’ context, logs and history can go a long way in evaluating risks and overall improving the security of your authentication process.

![]()
![]()
Compromised credentials
Know when credentials have been compromised. Through a set of tools and databases, you can keep an eye out for possible breeches and leaks of sensitive information.
![]()
![]()
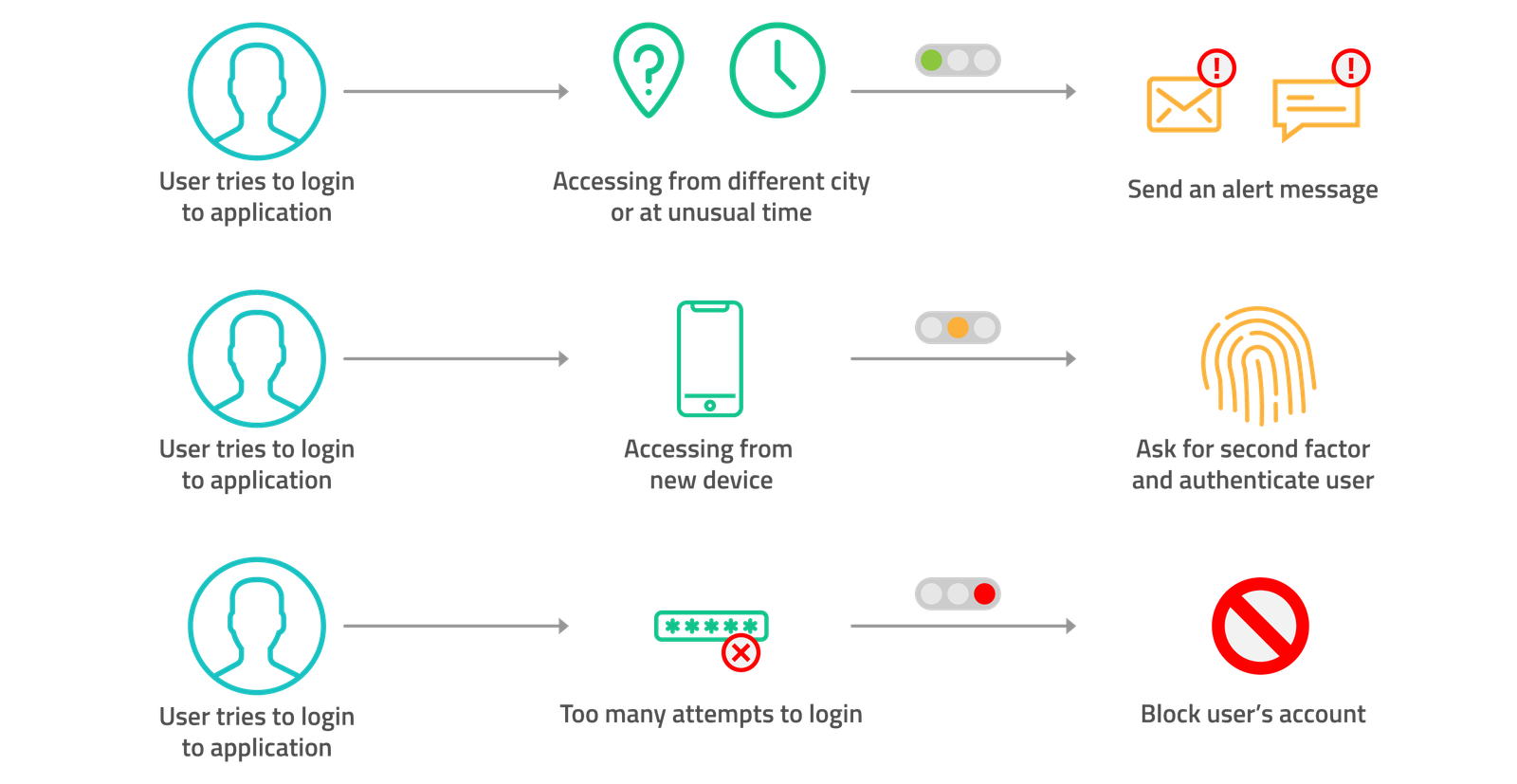
Login Anomaly and Fraud Detection
Based on context (such as location, time, device and network), login history and user behavior, our platform identifies anomalies during a user’s authentication, making it possible for specific actions to be applied (alert messages, second factors, account block, etc).
This feature also generates scores that can serve as a base for policy-making decisions throughout an account’s lifecycle.
![]()
![]()
Third-party Intelligence Integration
CoffeeBean integrates with multiple third-party solutions to increase the power of its authentication intelligence module and provides capabilities such as network reputation analysis, device fingerprinting and user behavior analytics.
![]()
![]()
Compromised credentials
Know when credentials have been compromised. Through a set of tools and databases, you can keep an eye out for possible breeches and leaks of sensitive information.
![]()
![]()
Login Anomaly and Fraud Detection
Based on context (such as location, time, device and network), login history and user behavior, our platform identifies anomalies during a user’s authentication, making it possible for specific actions to be applied (alert messages, second factors, account block, etc).
This feature also generates scores that can serve as a base for policy-making decisions throughout an account’s lifecycle.
![]()
![]()
Third-party Intelligence Integration
CoffeeBean integrates with multiple third-party solutions to increase the power of its authentication intelligence module and provides capabilities such as network reputation analysis, device fingerprinting and user behavior analytics.

Adaptive Authentication
Adaptive Authentication employs different information to understand whether to request an MFA, send an alert or block an account. This solution improves two important areas of your authentication system:
- Security: use multiple data sources and intelligence to evaluate the context and risk of an access
- User Experience: evaluate which authentication factor is the best to use in each scenario and ask for an MFA only when necessary.
![]()
![]()
Risk-based Authentication
By using the information from the Risk-Based Authentication, you can customize different flows on our platform, creating specific rules for different scenarios. For example, a user that accesses the account in a city that is not common for him/her receives an email alert, and a user that tries to access from a different device is asked for a second-factor of authentication.
![]()
![]()
Authentication Flows
By using the information from the risk-based Authentication you can customize different flows on our platform, creating specific rules for different scenarios. For example, a user that accesses the account in a city that is not common for him/her receives an email alert and a user that tries to access from a different device is asked for a second-factor.
![]()
![]()
Risk-based Authentication
By using the information from the Risk-Based Authentication, you can customize different flows on our platform, creating specific rules for different scenarios. For example, a user that accesses the account in a city that is not common for him/her receives an email alert, and a user that tries to access from a different device is asked for a second-factor of authentication.
![]()
![]()
Authentication Flows
By using the information from the risk-based Authentication you can customize different flows on our platform, creating specific rules for different scenarios. For example, a user that accesses the account in a city that is not common for him/her receives an email alert and a user that tries to access from a different device is asked for a second-factor.

Social Login
Social login allows customers to sign-in and sign-up through their social networks and not having to create and memorize passwords.
The social login also captures your customers’ social profile (with their consent) for personalized customer engagement and experience.